Briefly Describe the Best Practice Rules for Firewall Use
This may result in allowing every protocol through the firewall. Reinforce an individuals right to use or sell encryption algorithms without concern.
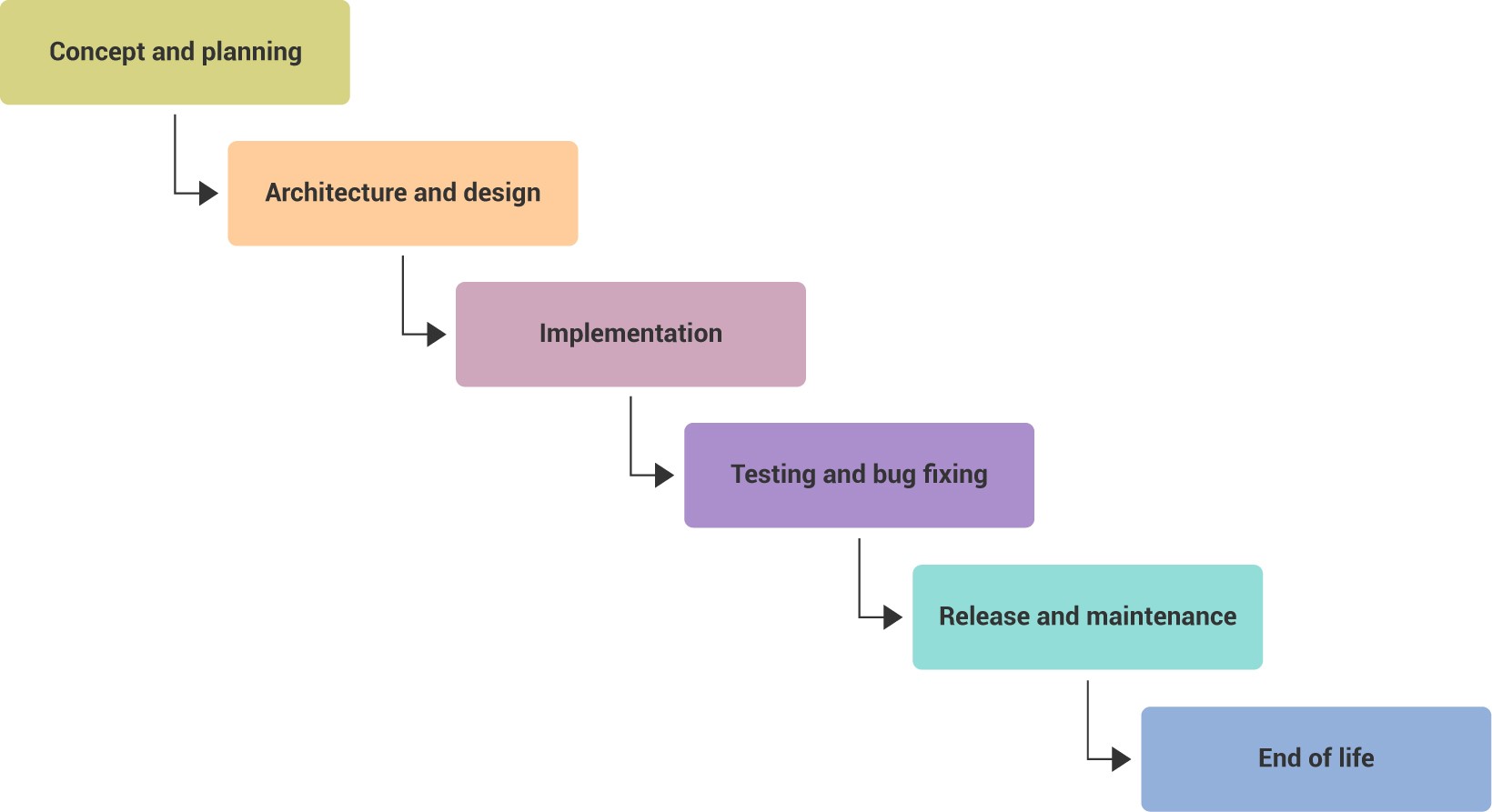
Secure Software Development Best Practices And Methodologies For Secure Sdl Lifecycle
Known as the ping service ICMP is an _____ and should be _____.
. We use various types of software which are downloaded from internet. An effective firewall doesnt just involve creating the right policies but also proactively analyzing the connections and filtering packets of data that pass through it. Essential feature turned on to save money b.
Briefly describe the best practice rules for firewall use. State that the use of encryption is not probable cause to suspect criminal activity. Briefly describe the best practice rules for firewall use.
In addition these practices should be regularly reviewed to measure their effectiveness and when necessary adjusted if circumstances change. Briefly describe the best practice rules for firewall use minimum 400 words. Prohibit the federal government from requiring the use of encryption for contracts grants and other official documents and correspondence.
Most of the time an update is a company plugging a security hole in their program. Three delete or deactivate any software programs or applications that youre not using. Allows members of the companyorganization to access services needed ii.
A firewall is software or firmware that prevents unauthorized access to a network. 105 Briefly describe the best practice rules for firewall use Graders Info 1 All from ICT 125 at Dublin City University. Briefly describe the best practice rules for firewall use minimum.
So I want to know about details of firewall. Briefly describe the best practice rules for firewall use200 Words 11. The process of adding deleting or modifying firewall rules should be well planned out Best practices firewall rules so that the performance of the existing rule set isnt negatively impacted.
BackBox is a market leader in network automation security and management solutions. The following are 10 essential best practices every organization should use to safeguard their enterprises today. These types of software may be harmful for our system.
Keep in mind these efforts must be ongoing in order to be successful. Never have the Allow All rule as your first rule. Briefly describe the seven best practices rules for firewall use.
Many organizations manage their firewall compliance requirements by turning on the firewall using most of the default settings and walking away. Unfortunately setting up a robust firewall that can protect your company in todays environment isnt easy or straightforward. These three actions are some of the best internet security practices for small business.
It inspects incoming and outgoing traffic using a set of rules to identify and block threats. Briefly describe the best practice rules for firewall use. Its better to have a Deny All rule as your first firewall rule and then add.
Firewalls are used in both personal and enterprise settings and many devices come with one built-in including Mac Windows and Linux computers. Chances are you arent using firewall best practices. Avoid using the Any option in the firewalls Allow rules.
We use the Firewall tools for security reasons. Known as the ping service ICMP is an _____ and should be _____. Ensure that your rules can identify the conditions within the connection predict what it will entail and detect disruptions in a normal connection.
Browse all Textbook Solutions. _____ firewalls are designed to operate at the media access control sublayer of the Question. False When Web services are offered outside the firewall SMTP traffic should be blocked from internal networks through the use of some form of proxy access or DMZ architecture.
While the final security options depend on the level of protection required and available budget there are some important tips and techniques to get started. Essential feature turned on to save money b. Not only that the existing rule set needs to be constantly optimized for speed and performance based on this carefully framed firewall rule base.
WLAN security best practice tips Enterprises should carefully plan and execute a cohesive strategy to protect their WLANs against data loss and unauthorized access. We help companies worldwide automate and streamline complex tasks ensure network health and performance achieve business continuity and do more with fewer resources. Up to 75 cash back Two always keep software up to date.
All traffic from the trusted network is allowed out i.

Azure Security Best Practices You Need To Know Cloud Academy

7 Best Practices For Securing System Administrator Privileged Account Ekran System

Iso 27002 Best Practices For Information Security Management

Top 6 Best Practices For Website Uptime Monitoring

7 Best Practices For Securing System Administrator Privileged Account Ekran System

Azure Governance Best Practices Azure Talk

Best Practices For Securing Active Directory Manualzz

7 Best Practices For Securing System Administrator Privileged Account Ekran System

Ibm Tivoli Network Manager Ip Edition Best Practices Guide 1 0 Manualzz

Azure Governance Best Practices Azure Talk
Hybrid Deployment Best Practices Microsoft Tech Community

7 Best Practices For Securing System Administrator Privileged Account Ekran System
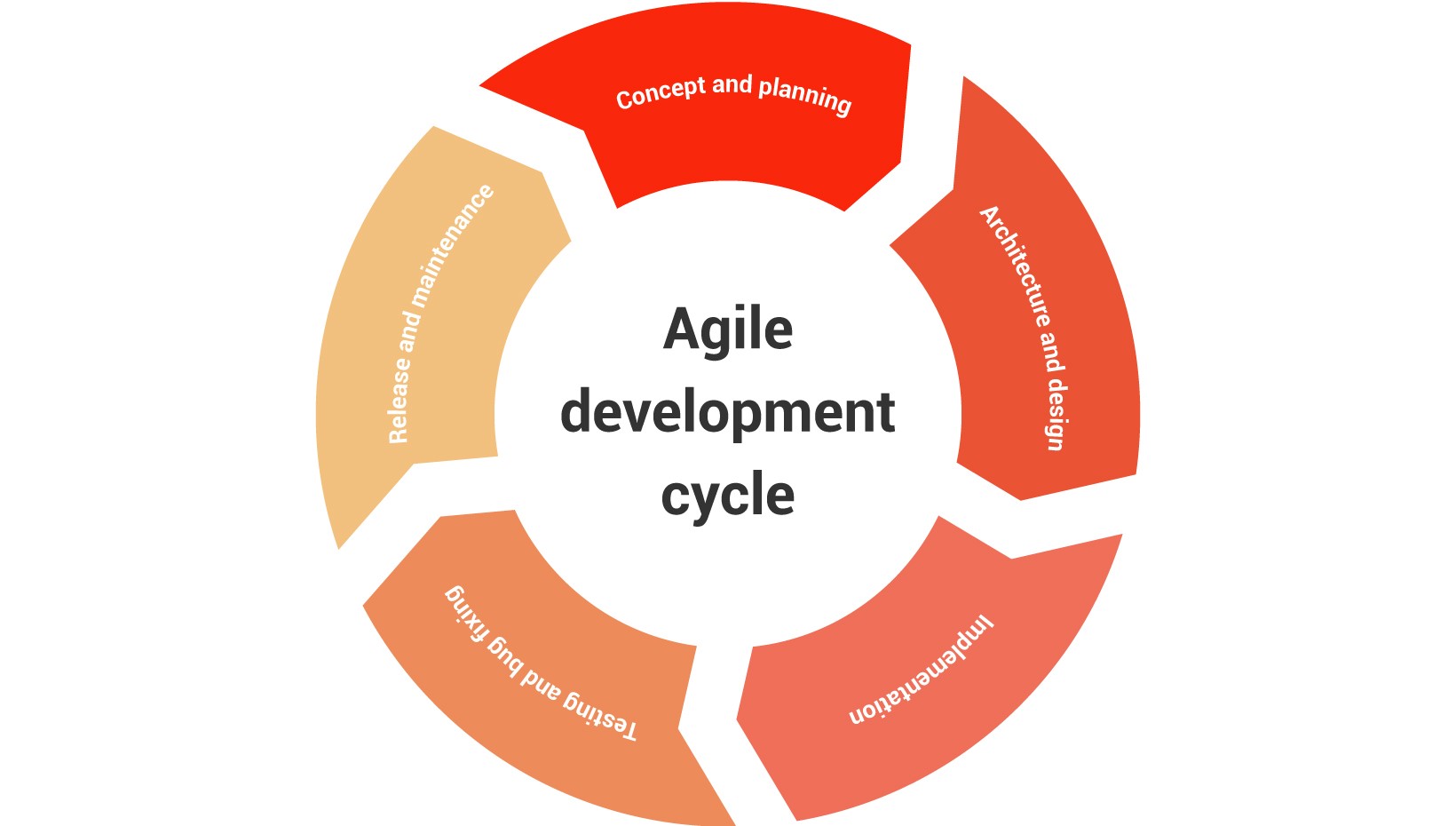
Secure Software Development Best Practices And Methodologies For Secure Sdl Lifecycle

Azure Security Best Practices You Need To Know Cloud Academy

7 Best Practices For Securing System Administrator Privileged Account Ekran System


Comments
Post a Comment